How To Invoke Rest Webservice In Java With No Md5 Hash And With Updated Aes Algorithms
The gist of hallmark is to provide users with a set of credentials, such as username and password, and to verify that they provide the right credentials whenever they want access to the application. Hence, we need a way to store these credentials in our database for future comparisons. However, storing passwords on the server side for hallmark is a difficult job. Let'southward explore 1 of the mechanisms that brand password storage secure and easier: hashing.
Storing Passwords is Risky and Complex
A simple approach to storing passwords is to create a table in our database that maps a username with a countersign. When a user logs in, the server gets a request for hallmark with a payload that contains a username and a password. We look upwards the username in the table and compare the countersign provided with the password stored. A match gives the user access to the application.
The security strength and resilience of this model depends on how the password is stored. The most basic, but besides the least secure, countersign storage format is cleartext .
Every bit explained past Dan Cornell from the Denim Group, cleartext refers to "readable data transmitted or stored in the articulate", for instance, unencrypted. Yous may accept as well seen the terms plaintext and plain text . What'south the difference? Co-ordinate to Cornell, plaintext refers to information that volition serve as the input to a cryptographic algorithm, while plain text refers to unformatted text, such as the content of a apparently text file or .txt. Information technology'south of import to know the stardom betwixt these terms equally we move forward.
Storing passwords in cleartext is the equivalent of writing them down in a slice of digital paper. If an attacker was to pause into the database and steal the passwords table, the assailant could so access each user business relationship. This problem is compounded past the fact that many users re-use or apply variations of a unmarried password, potentially allowing the assailant to access other services unlike from the one being compromised. That all sounds like a security nightmare!
The set on could come from within the organization. A rogue software engineer with admission to the database could corruption that access power, retrieve the cleartext credentials, and access any business relationship.
A more secure way to store a countersign is to transform it into data that cannot be converted back to the original countersign. This mechanism is known as hashing . Let's learn more well-nigh the theory behind hashing, its benefits, and its limitations.
"We must baby-sit user accounts from both internal and external unauthorized access. Cleartext storage must never be an option for passwords. Hashing and salting should always be part of a password direction strategy."

Tweet This
What's Hashing About?
Past lexicon definition, hashing refers to "chopping something into small pieces" to make it look like a "confused mess". That definition closely applies to what hashing represents in computing.
In cryptography, a hash part is a mathematical algorithm that maps data of whatsoever size to a chip cord of a fixed size. We can refer to the function input as message or merely equally input. The fixed-size string function output is known as the hash or the bulletin digest . As stated by OWASP, hash functions used in cryptography have the post-obit cardinal properties:
- Information technology'southward easy and practical to compute the hash, but "hard or impossible to re-generate the original input if only the hash value is known."
- It'south difficult to create an initial input that would match a specific desired output.
Thus, in contrast to encryption, hashing is a one-way mechanism. The data that is hashed cannot be practically "unhashed".
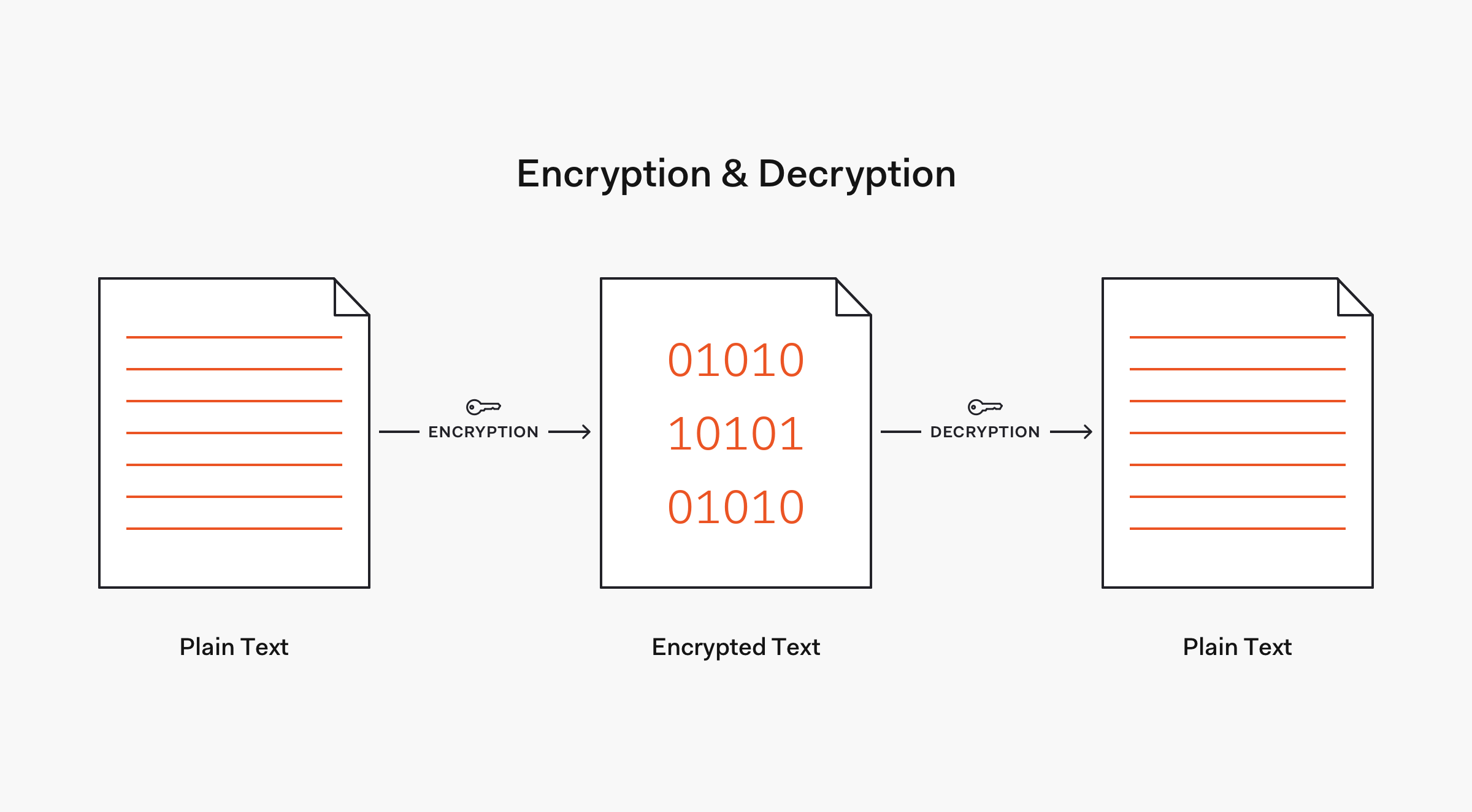
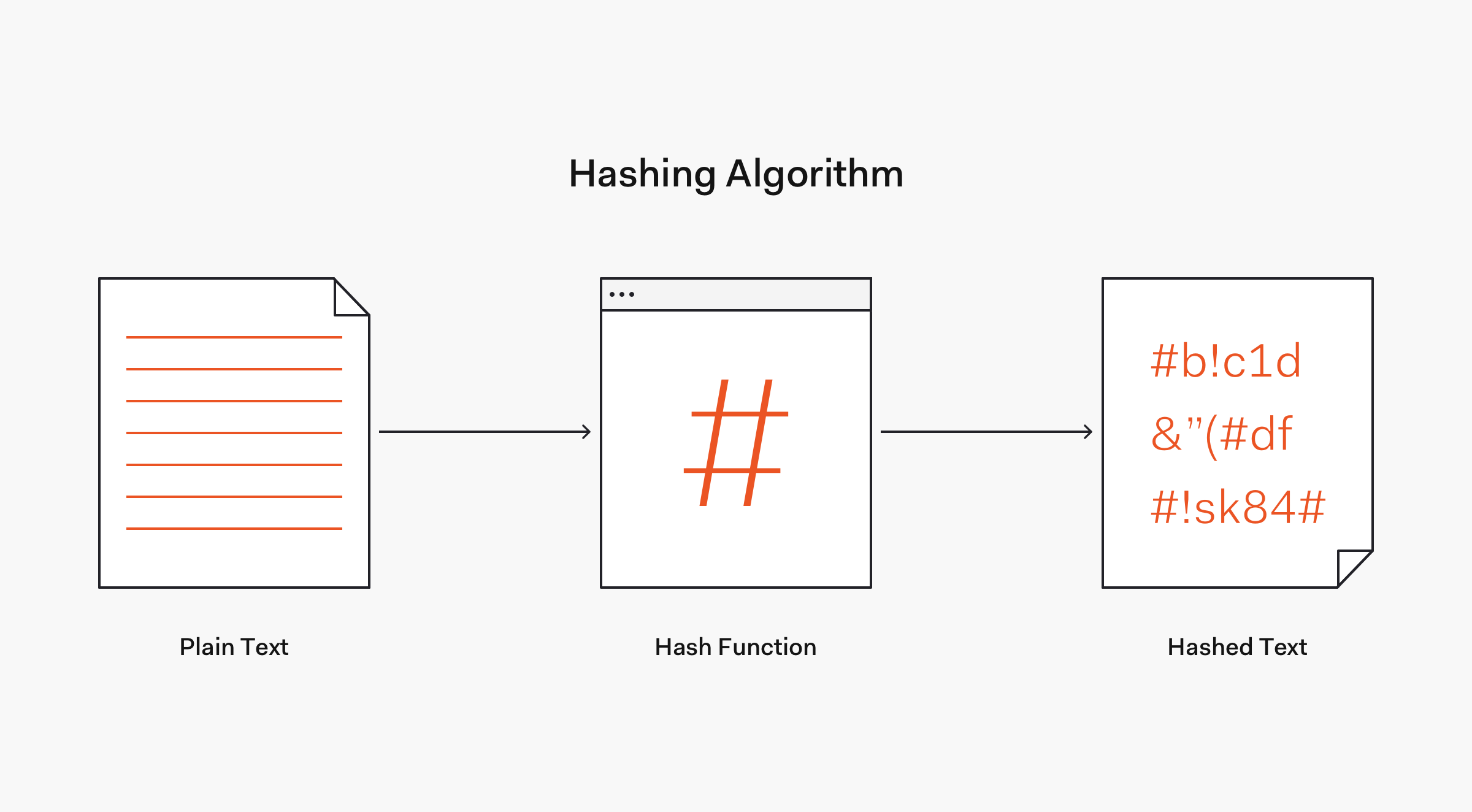
Commonly used hashing algorithms include Message Digest (MDx) algorithms, such as MD5, and Secure Hash Algorithms (SHA), such equally SHA-1 and the SHA-ii family that includes the widely used SHA-256 algorithm. Later on, we are going to larn nearly the strength of these algorithms and how some of them have been deprecated due to rapid computational advancements or have fallen out of use due to security vulnerabilities.
In bitcoin, integrity and block-chaining employ the SHA-256 algorithm as the underlying cryptographic hash role. Allow's expect at a hashing example using SHA-256 and Python.
If y'all want to follow along, you tin use the online Python repl.information technology IDE to run Python scripts hands.
The Python repl.information technology IDE provides you with a code editor to enter Python code, buttons to save or run the script, and a console to visualize the script output.
In the code editor, enter the following command to import the constructor method of the SHA-256 hash algorithm from the hashlib module:
from hashlib import sha256 In the line below, create an instance of the sha256 class:
h = sha256( ) Side by side, use the update ( ) method to update the hash object:
h.update( b'python1990K00L' ) So, use the hexdigest ( ) method to become the digest of the cord passed to the update ( ) method:
hash = h.hexdigest( ) The digest is the output of the hash part.
Finally, print the hash variable to run into the hash value in the console:
print ( hash ) The consummate script looks similar this:
from hashlib import sha256 h = sha256( ) h.update( b'python1990K00L' ) hash = h.hexdigest( ) print ( hash ) To run the script, click on the "run" push button at the top of the screen. On the console, you should see the following output:
d1e8a70b5ccab1dc2f56bbf7e99f064a660c08e361a35751b9c483c88943d082 To epitomize, you lot provide the hash office a string equally input and get back another string as output that represents the hashed input:
Input:
python1990K00L
Hash (SHA-256):
d1e8a70b5ccab1dc2f56bbf7e99f064a660c08e361a35751b9c483c88943d082
Effort hashing the string python. Did you go the following hash?
11a4a60b518bf24989d481468076e5d5982884626aed9faeb35b8576fcd223e1 "Understanding blockchains and cryptocurrency, such as bitcoin, is easier when you sympathise how cryptographic hash functions work."

Tweet This
Using SHA-256, we have transformed a random-size input into a stock-still-size scrap string. Notice how, despite the length difference between python1990K00L and python, each input produces a hash of the same length. Why's that?
Using hexdigest ( ) , you produced a hexadecimal representation of the hash value. For whatsoever input, each bulletin digest output in hexadecimal format has 64 hexadecimal digits. Each digit pair represent a byte. Thus, the digest has 32 bytes. Since each byte holds 8 bits of information, the hash string represent 256 $.25 of data in total. For this reason, this algorithm is called SHA-256 and all of its inputs have an output of equal size.
Some hash functions are widely used only their backdrop and requirements practice non provide security. For instance, cyclic back-up cheque (CRC) is a hash function used in network applications to discover errors merely it is not pre-prototype resistant, which makes it unsuitable for use in security applications such equally digital signatures.
Throughout this article, we are going to explore the properties that make a hash office suitable for usage in security applications. To showtime, we should know that even if we were to find the details on how the input to a cryptographic hash office gets computed into a hash, it would not exist practical for us to opposite the hash back into the input. Why'due south that?
Cryptographic Hash Functions are Practically Irreversible
Hash functions behave as ane-fashion functions by using mathematical operations that are extremely difficult and cumbersome to revert such as the modulo operator.
The modulo operator gives usa the remainder of a division. For example, 5 modern 3 is 2 since the residue of 5 / 3 is two using integer division. This operation is deterministic, given the same input always produces the same output: mathematically, five / three ever results in two . However, an of import characteristic of a modulo operation is that we cannot discover the original operands given the result. In that sense, hash functions are irreversible.
Knowing that the result of a modulo operation is ii but tells u.s. that ten divided by y has a reminder of 2 just it doesn't tell the states anything near 10 and y. There is an infinite number of values that could exist substituted for 10 and y for x mod y to render 2 :
seven mod 5 = 2 9 modern 7 = 2 two mod 3 = 2 x mod eight = 2 ... When using a cryptographic hash office, we must not be able to find a pre-epitome by looking at a hash . A pre-prototype is what we call a value that produces a certain specific hash when used as input to a hash office — the plaintext value. Hence, a cryptographic hash function is designed to be resistant to pre-image attacks; it must be pre-prototype resistant . And then if an attacker knows a hash, it is computationally infeasible to find any input that hashes to that given output. This holding is what makes hashing one of the foundations of bitcoin and blockchains.
If you are curious nigh how a hash function works, this Wikipedia article provides all the details most how the Secure Hash Algorithm 2 (SHA-2) works.
A Small Change Has a Large Impact
Another virtue of a secure hash part is that its output is non piece of cake to predict. The hash for dontpwnme4 would be very different than the hash of dontpwnme5, even though only the last character in the string changed and both strings would be adjacent in an alphabetically sorted list:
Input:
dontpwnme4
Hash (SHA-256):
4420d1918bbcf7686defdf9560bb5087d20076de5f77b7cb4c3b40bf46ec428b
Input:
dontpwnme5
Hash (SHA-256):
threefc79ff6a81da0b5fc62499d6b6db7dbf1268328052d2da32badef7f82331dd6
Here'south the Python script used to calculate these values in case you demand it:
from hashlib import sha256 h = sha256( ) h.update( b'<Cord>' ) hash = h.hexdigest( ) print ( hash ) Replace < Cord > with the desired string to hash and run it on repl.it.
This property is known as the avalanche effect and it has the desirable outcome that if an input is inverse slightly, the output is inverse significantly.
Consequentially, there is no feasible way for us to determine what the hash of dontpwnme6 would be based on the 2 previous hashes; the output is non-sequential.
Using Cryptographic Hashing for More Secure Countersign Storage
The irreversible mathematical backdrop of hashing go far a phenomenal mechanism to conceal passwords at remainder and in motion. Another critical property that makes hash functions suitable for countersign storage is that they are deterministic.
A deterministic function is a function that given the same input always produces the aforementioned output. This is vital for authentication since we need to have the guarantee that a given password will e'er produce the same hash; otherwise, it would be impossible to consistently verify user credentials with this technique.
To integrate hashing in the password storage workflow, when the user is created, instead of storing the password in cleartext, we hash the password and store the username and hash pair in the database tabular array. When the user logs in, nosotros hash the countersign sent and compare it to the hash connected with the provided username. If the hashed countersign and the stored hash match, we have a valid login. It'southward important to note that we never store the cleartext password in the process, we hash it and so forget it.
Whereas the transmission of the password should be encrypted, the password hash doesn't need to be encrypted at balance. When properly implemented, password hashing is cryptographically secure. This implementation would involve the use of a salt to overcome the limitations of hash functions.
Uniqueness is the central property for salts; length happens to assist uniqueness.
Limitations of Hash Functions
Hashing seems pretty robust. But if an aggressor breaks into the server and steals the password hashes, all that the attacker tin can see is random-looking data that can't be reversed to plaintext due to the architecture of hash functions. An aggressor would need to provide an input to the hash function to create a hash that could and then be used for authentication, which could exist washed offline without raising any red flags on the server.
The attacker could then either steal the cleartext countersign from the user through modernistic phishing and spoofing techniques or try a brute forcefulness set on where the attacker inputs random passwords into the hash function until a matching hash is found.
A brute-strength attack is largely inefficient considering the execution of hash functions tin can be configured to exist rather long. This hashing speed bump will be explained in more than detail later. Does the attacker have whatever other options?
Since hash functions are deterministic (the same role input ever results in the same hash), if a couple of users were to use the aforementioned countersign, their hash would exist identical. If a significant corporeality of people are mapped to the aforementioned hash that could be an indicator that the hash represents a commonly used password and let the attacker to significantly narrow down the number of passwords to use to suspension in by fauna force.
Additionally, through a rainbow table attack , an aggressor tin can use a large database of precomputed hash bondage to notice the input of stolen password hashes. A hash chain is 1 row in a rainbow table, stored as an initial hash value and a final value obtained later on many repeated operations on that initial value. Since a rainbow tabular array attack has to re-compute many of these operations, nosotros can mitigate a rainbow table attack by boosting hashing with a procedure that adds unique random information to each input at the moment they are stored. This practice is known as calculation salt to a hash and information technology produces salted password hashes .
With a salt, the hash is not based on the value of the password lone. The input is made up of the countersign plus the salt. A rainbow table is congenital for a prepare of unsalted hashes. If each pre-paradigm includes a unique, unguessable value, the rainbow table is useless. When the aggressor gets a hold of the salt, the rainbow table now needs to be re-computed, which ideally would accept a very long fourth dimension, further mitigating this assault vector.
"The trick is to ensure the effort to "break" the hashing exceeds the value that the perpetrators will gain by doing so. None of this is nigh being "unhackable"; it's almost making the difficulty of doing so not worth the effort." - Troy Hunt
No Need for Speed
According to Jeff Atwood, "hashes, when used for security, need to be slow." A cryptographic hash function used for password hashing needs to be boring to compute because a rapidly computed algorithm could brand brute-force attacks more feasible, especially with the rapidly evolving power of modern hardware. We can achieve this by making the hash calculation tedious by using a lot of internal iterations or by making the calculation retentiveness intensive.
A slow cryptographic hash function hampers that process simply doesn't bring it to a halt since the speed of the hash computation affects both well-intended and malicious users. Information technology'due south important to achieve a good residue of speed and usability for hashing functions. A well-intended user won't have a noticeable operation affect when trying a single valid login.
Collision Attacks Deprecate Hash Functions
Since hash functions can take an input of whatever size only produce hashes that are fixed-size strings, the ready of all possible inputs is infinite while the gear up of all possible outputs is finite. This makes it possible for multiple inputs to map to the same hash. Therefore, even if we were able to reverse a hash, nosotros would non know for sure that the effect was the selected input. This is known every bit a standoff and it'south not a desirable effect.
A cryptographic collision occurs when ii unique inputs produce the same hash. Consequently, a collision assail is an attempt to notice ii pre-images that produce the same hash. The attacker could apply this collision to fool systems that rely on hashed values by forging a valid hash using wrong or malicious information. Therefore, cryptographic hash functions must also be resistant to a collision attack by making it very difficult for attackers to find these unique values.
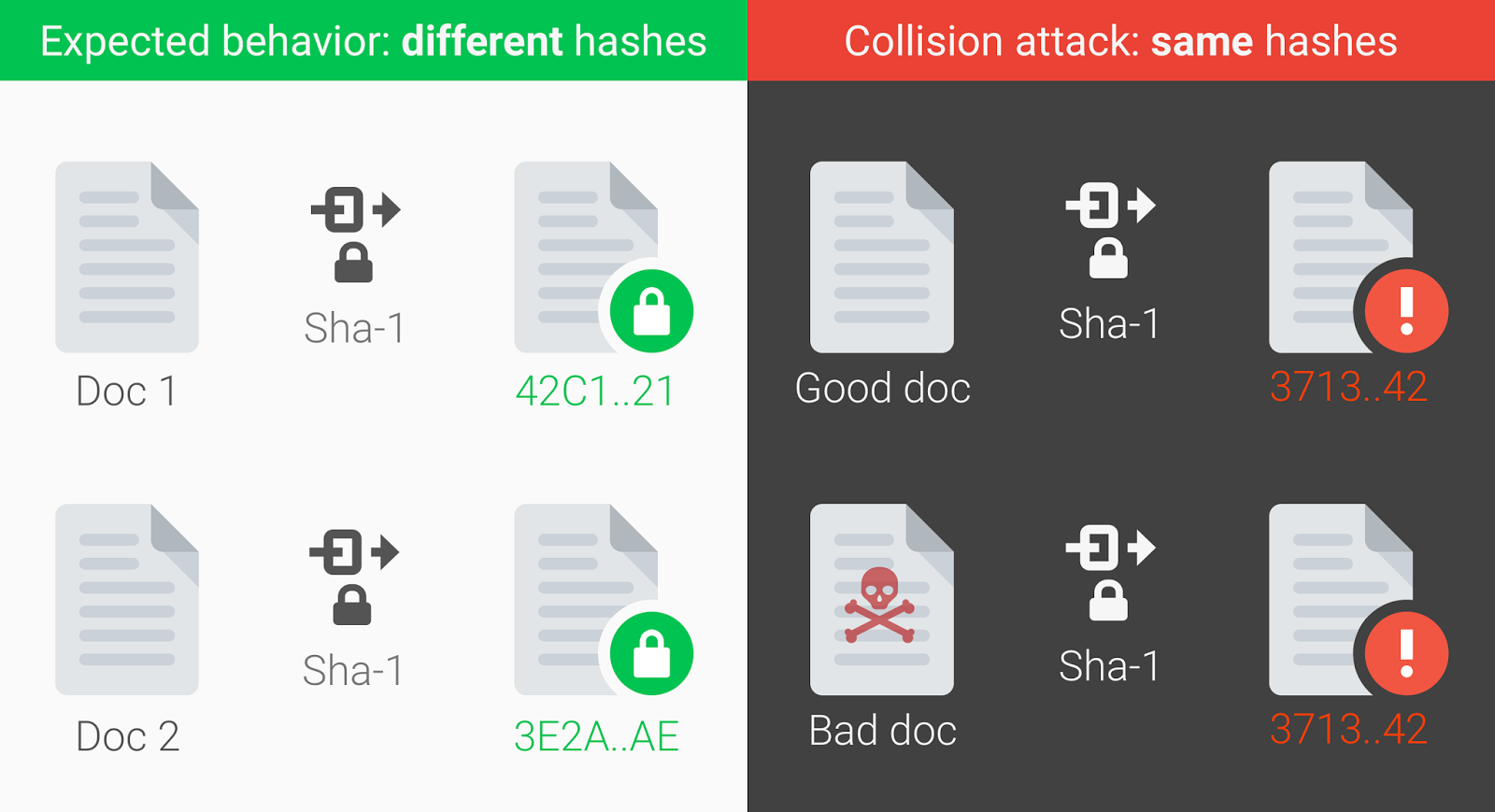
Source: Announcing the first SHA1 collision (Google)
"Since inputs can be of infinite length but hashes are of a fixed length, collisions are possible. Despite a standoff risk existence statistically very low, collisions have been found in unremarkably used hash functions."

Tweet This
For unproblematic hashing algorithms, a simple Google search will let us to observe tools that catechumen a hash back to its cleartext input. The MD5 algorithm is considered harmful today and Google announced the first SHA1 standoff in 2017. Both hashing algorithms have been deemed dangerous to apply and deprecated by Google due to the occurrence of cryptographic collisions.
Google recommends using stronger hashing algorithms such as SHA-256 and SHA-3. Other options normally used in do are bcrypt, scrypt, among many others that y'all tin find in this list of cryptographic algorithms. However, as nosotros've explored earlier, hashing lonely is not sufficient and should be combined with salts. Learn more near how calculation salt to hashing is a better mode to shop passwords.
Recap
Let'south recap what we've learned through this article:
- The core purpose of hashing is to create a fingerprint of data to assess data integrity.
- A hashing part takes arbitrary inputs and transforms them into outputs of a fixed length.
- To authorize as a cryptographic hash part, a hash function must be pre-image resistant and standoff resistant.
- Due to rainbow tables, hashing lone is not sufficient to protect passwords for mass exploitation. To mitigate this assail vector, hashing must integrate the employ of cryptographic salts.
- Password hashing is used to verify the integrity of your password, sent during login, against the stored hash so that your actual password never has to exist stored.
- Non all cryptographic algorithms are suitable for the modernistic industry. At the time of this writing, MD5 and SHA-1 have been reported past Google as being vulnerable due to collisions. The SHA-2 family stands every bit a improve option.
Simplifying Password Management with Auth0
You can minimize the overhead of hashing, salting, and countersign management through Auth0. We solve the near complex identity use cases with an extensible and easy to integrate platform that secures billions of logins every calendar month.
Auth0 helps you prevent critical identity data from falling into the wrong hands. We never store passwords in cleartext. Passwords are always hashed and salted using bcrypt. Additionally, data encryption is offered at rest and in transit by using TLS with at least 128-bit AES encryption. Nosotros've built land-of-the-art security into our product, to protect your business and your users.
Make the internet safer, sign up for a costless Auth0 account today.
How To Invoke Rest Webservice In Java With No Md5 Hash And With Updated Aes Algorithms,
Source: https://auth0.com/blog/hashing-passwords-one-way-road-to-security/
Posted by: perezboading73.blogspot.com


0 Response to "How To Invoke Rest Webservice In Java With No Md5 Hash And With Updated Aes Algorithms"
Post a Comment